搜索结果: 1-15 共查到“Too Simple”相关记录782条 . 查询时间(0.64 秒)
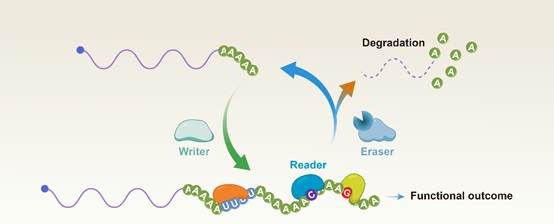
中国科学院遗传与发育生物学研究所陆发隆研究组应邀在Trends in Biochemical Sciences撰写题为“Beyond simple tails: poly(A) tail-mediated RNA epigenetic regulation”的综述文章(图)
陆发隆 真核生物 基因
2024/8/11
2024年7月14日,Trends in Biochemical Sciences杂志在线发表了中国科学院遗传与发育生物学研究所陆发隆研究组撰写的题为“Beyond simple tails: poly(A) tail-mediated RNA epigenetic regulation”的综述论文(DOI:10.1016/j.tibs.2024.06.013)。该论文总结了近年来关于RNA po...
Empowering Forest Owners with Simple Volume Equations for Poplar Plantations in the órbigo River Basin (NW Spain)
tree plantations growth equations rotation length growth rates poplar productivity
2024/1/11
Hybrid poplar plantations are becoming increasingly important as a source of income for farmers in northwestern Spain, as rural depopulation and farmers aging prevent landowners from planting other la...
Academy of Mathematics and Systems Science, CAS Colloquia & Seminars:Unit commitment problems and their compact and simple models, algorithms, and applications
Unit commitment problems 机组组合 电力系统优化
2023/4/14

When curved materials flatten, simple geometry can predict the wrinkle patterns that emerge(图)
弯曲材料 皱纹图案 柔性电子产品
2023/7/7

Simple new testing method aims to improve time-release drugs(图)
new testing method aims improve time-release drugs
2020/12/11
When you take a time-release drug, you count on it doing what the package says: release the drug slowly into your bloodstream to provide benefits over the specified period of time. When the drug disso...
Researchers at Carnegie Mellon University have developed an efficient new way to quickly analyze complex geometric models by borrowing a computational approach that made photorealistic anima...
Simple and Efficient KDM-CCA Secure Public Key Encryption
key dependent message security chosen ciphertext security
2019/9/16
We propose two efficient public key encryption (PKE) schemes satisfying key dependent message security against chosen ciphertext attacks (KDM-CCA security). The first one is KDM-CCA secure with respec...
In 1998, Jerey Hostein, Jill Pipher, and Joseph H. Silverman introduced the famous Ntru cryptosystem, and called it "A ring-based public key cryptosystem". Actually it turns out to be a lattice based ...
CCA-Secure Leakage-Resilient Identity-Based Key-Encapsulation from Simple (not $\mathtt{q}$-type) Assumptions
public-key cryptography leakage-resilient identity-based encryption
2019/8/30
In this paper, we propose a new leakage-resilient identity-based encryption (IBE) scheme that is secure against chosen-ciphertext attacks (CCA) in the bounded memory leakage model. It is the first CCA...
Practical Attribute Based Inner Product Functional Encryption from Simple Assumptions
Functional Encryption Attribute Based Encryption Inner Product
2019/7/23
Functional encryption (FE) that bases on user attributes has many useful practical applications. For example, a company may only authorize department heads of other sections to query the average sale ...
Simple and Efficient Approach for Achieving End-to-End Anonymous Communication
cryptographic protocols Anonymous communication
2019/7/15
Anonymous communication, that is secure end-to-end and unlinkable, plays a critical role in protecting user privacy by preventing service providers from using message metadata to discover communicatio...

Engineers create a simple test that can measure stress(图)
Engineers simple test measure stress
2019/10/28
National Science Foundation-funded researchers at the University of Cincinnati developed a new technology that can easily test and measure common stress hormones in sweat, blood, urine or saliva. Even...
Simple Yet Efficient Knowledge-Sound and Non-Black-Box Any-Simulation-Extractable ZK-SNARKs
NIZK QAP QSP
2019/6/4
Motivated by applications like verifiable computation and privacy-preserving cryptocurrencies, many efficient pairing-based SNARKs were recently proposed. However, the most efficient SNARKs like the o...
A Modified Simple Substitution Cipher With Unbounded Unicity Distance
finite-key unicity randomization
2019/6/4
The classic simple substitution cipher is modified by randomly inserting key-defined noise characters into the ciphertext in encryption which are ignored in decryption. Interestingly, this yields a fi...
Simple Schemes in the Bounded Storage Model
Bounded Storage Model Commitment Oblivious Transfer
2019/5/21
The bounded storage model promises unconditional security proofs against computationally unbounded adversaries, so long as the adversary’s space is bounded. In this work, we develop simple new constru...


